
Yeeeep! Cisco Cyber Ops Scholarship
I have really exciting news:


I have really exciting news:

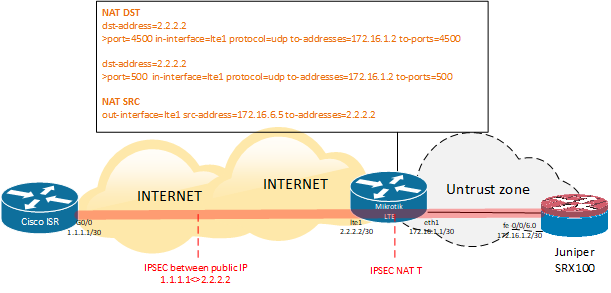
Since my company has been using Cisco and Juniper network equipment we have a lot of IPSec tunnels to remote branches. To achieve some sort of high-availability we have decided to implement one of the IPSec tunnels over an LTE network.
To do so we bought Mikrotik wAP LTE kit to get connected to an LTE network and obtained a public IP address from a mobile data operator.
So.. we have:

Cisco ISR config
Tunnel interface:
|
1 2 3 4 5 6 7 8 9 10 |
interface Tunnel10 description TO REMOTE BRANCH bandwidth 15000 ip address 172.20.1.1 255.255.255.252 ip mtu 1400 ip tcp adjust-mss 1360 tunnel source GigabitEthernet0/0/0 tunnel mode ipsec ipv4 tunnel destination 2.2.2.2 tunnel protection ipsec profile VTI |
|
1 |
ip route 2.2.2.2 255.255.255.255 1.1.1.2 |
IPSec config:
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 |
crypto isakmp policy 1 encr 3des authentication pre-share group 2 crypto isakmp key SHAREDKEY address 10.0.0.2 crypto isakmp invalid-spi-recovery crypto isakmp keepalive 10 ! ! crypto ipsec transform-set TSET esp-3des esp-sha-hmac mode tunnel ! crypto ipsec profile VTI set transform-set TSET ! ! ! ! ! ! ! interface Tunnel10 bandwidth 15000 ip address 172.20.1.1 255.255.255.252 ip mtu 1400 ip tcp adjust-mss 1360 tunnel source Ethernet0/0 tunnel mode ipsec ipv4 tunnel destination 2.2.2.2 tunnel protection ipsec profile VTI ! |
Juniper SRX config
|
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 |
security { ike { policy IKE_DC { mode main; proposal-set compatible; pre-shared-key ascii-text "SHAREDPASS"; ## SECRET-DATA } gateway GW_DC { ike-policy IKE_DC; address 1.1.1.1; external-interface fe-0/0/6.0; } } ipsec { policy Juniper { proposal-set compatible; } vpn VPN_DC { bind-interface st0.10; ike { gateway GW_DC; ipsec-policy Juniper; } establish-tunnels immediately; } } alg { dns disable; } flow { tcp-mss { ipsec-vpn { mss 1360; } } } |
Adding to zone and allowing IKE on the interface:
|
1 2 |
set security zones security-zone untrust interfaces fe-0/0/6.0 set security zones security-zone untrust host-inbound-traffic system-services ike |
Mikrotik config
|
1 2 3 4 5 6 7 |
/ip firewall nat add action=dst-nat chain=dstnat dst-address=2.2.2.2 dst-port=4500 \ in-interface=lte1 protocol=udp to-addresses=172.16.1.2 to-ports=4500 add action=dst-nat chain=dstnat dst-address=2.2.2.2 dst-port=500 \ in-interface=lte1 protocol=udp to-addresses=172.16.1.2 to-ports=500 add action=src-nat chain=srcnat out-interface=lte1 src-address=172.16.1.2 \ to-addresses=2.2.2.2 |
IPsec debug on SRX
To debug IPSec on Juniper you can use this commands:
Phase 1
|
1 2 3 4 5 6 7 8 9 10 11 |
show security ike security-associations node0: -------------------------------------------------------------------------- Index State Initiator cookie Responder cookie Mode Remote Address 1990848 UP 0a8d1bb614de2965 47ade7df5b93f10f Main 1.1.1.1 show security ike security-association index <#> detail show security ike security-association <peer-ip> show security ike stats sa |
Phase 2
|
1 2 3 4 5 6 7 8 9 10 11 12 13 |
show security ipsec security-associations | no-more node0: -------------------------------------------------------------------------- Total active tunnels: 3 ID Algorithm SPI Life:sec/kb Mon lsys Port Gateway <131073 ESP:3des/sha1 828f5d73 1299/ 4426652 - root 500 1.1.1.1 >131073 ESP:3des/sha1 3c0637c3 1299/ 4426652 - root 500 1.1.1.1 show security ipsec inactive-tunnels node0: -------------------------------------------------------------------------- Total inactive tunnels: 0 Total inactive tunnels with establish immediately: 0 |

Due to a lot of experience that I have with real networking hardware, it is not mandatory to have a Home Lab to pass CCNA R&S. However, I’ve decided that it could be extremely useful for my further professional development to have a lab at home.
It is understood that there are two options:
Option 1. Buy real Cisco gear on Ebay

“+”
“-“
I have been around networks for over 8 years and I always have had a dream to become a CCIE. Now It is time to set the GOAL and to start my journey.
So that I’ve started studying for the CCNA R&S exam and thought I would put my notes on this blog. It might be useful for me and hopefully, my notes can be helpful to someone else. These notes are based on CCNAR&S 200-125 Official Cert Guide and CBT Nuggets.
Many people have trouble understanding cisco’s native vlan idea. Actually, it is very simple.
Let’s start with statement, that the native VLAN has two functions: